IoT Spy Device
IoT, or Internet of Things, refers to the collective network of connected devices and the technology that facilitates communication between devices and the cloud, as well as between the devices themselves.
Akhil, a cybersecurity researcher, receives an unusual request from a friend: “I think my smartwatch is spying on me. Can you check it out?ˮ Intrigued, Akhil accepts the challenge.
Little does he know, this investigation will turn into a full-fledged security audit, revealing a hidden threat disguised as an innocent fitness tracker.
Phase 1:
Reconnaissance & OSINT
Before tearing apart the smartwatch, Akhil gathers Open-Source Intelligence (OSINT) to learn about its internals.
Tasks:
- Identify the Manufacturer & Model – Checking the FCC ID reveals the manufacturer and certification details.
- Analyze Online Documentation – Searching for datasheets, teardown videos, and known vulnerabilities.
- Component Identification – Determining the CPU, Bluetooth module, and storage type based on OSINT findings.
Key Concepts:
- FCC ID Lookup – Helps identify internal schematics and chipsets.
- Chipset Analysis – Determines if the smartwatch runs on ARM Cortex, RISC-V, or a proprietary system.
- Bluetooth Security – Investigates if the device is using insecure Bluetooth pairing, exposing it to attacks.
Phase 2:
Hardware Inspection & Debugging
Akhil carefully disassembles the smartwatch, searching for debugging interfaces.
Tasks:
- Locate Debugging Ports – Finding exposed UART, JTAG, or SWD interfaces.
- Connect to UART/JTAG – Establishing communication with a debugging tool.
- Dump the Firmware – Extracting the firmware for analysis.
Tools & Techniques:
- Multimeter & Oscilloscope – Helps trace active pins and voltage levels.
- USB-to-UART Adapter (e.g., CP2102, FTDI) – Enables interaction with serial consoles.
- JTAGulator – Auto-detects JTAG pinouts.
- Flashrom – Reads firmware from onboard flash memory.
Debugging Interfaces:
- UART (Universal Asynchronous Receiver-Transmitter) – Often provides a serial console.
- JTAG (Joint Test Action Group) – Grants deep debugging capabilities.
- SWD (Serial Wire Debug) – ARM-specific debugging alternative.
Phase 3:
Firmware Extraction & Static Analysis
With a successful firmware dump, Akhil examines its contents.
Tasks:
- Extract Filesystem & Binaries – Identifying and extracting crucial files.
- Analyze Strings & Configuration Files – Searching for hardcoded credentials and API endpoints.
- Identify Network Activity – Detecting suspicious outbound connections.
Tools:
- Binwalk – Extracts and analyzes firmware images.
- Strings – Searches for readable text within binaries.
- Ghidra / IDA Pro – Reverse engineering tools.
- Radare2 – A lightweight alternative for binary analysis.
Example Commands:
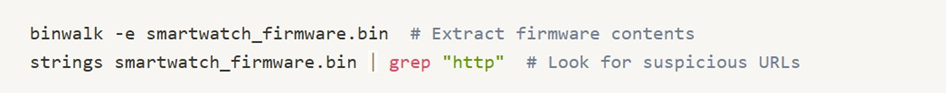
Suspicious Findings:
While analyzing the extracted files, Akhil stumbles upon a hardcoded URL pointing to an external server in China. Running strings on one of the binaries reveals the following:
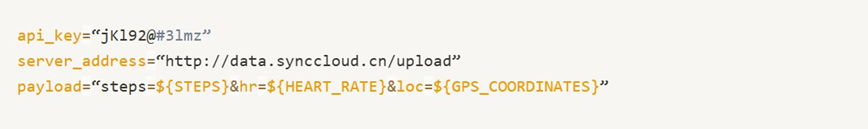
This confirms the device is transmitting user data without consent.
Phase 4:
Behavioral Analysis & Network Monitoring
Akhil sets up a controlled environment to monitor the smartwatchʼs real-time behavior.
Tasks:
- Monitor Network Traffic – Capturing packets to inspect data transmission.
- Analyze Companion App – Checking for unnecessary permissions.
- Emulate the Firmware – Running the firmware in a sandboxed environment.
Tools:
- Wireshark – Captures and analyzes network packets.
- Mitmproxy – Intercepts and modifies HTTP/S traffic.
- Frida – Hooks into the smartwatch app for deeper analysis.
- QEMU – Emulates the smartwatchʼs firmware.
Packet Capture Output:
Akhil records outgoing network traffic and finds the following log snippet:
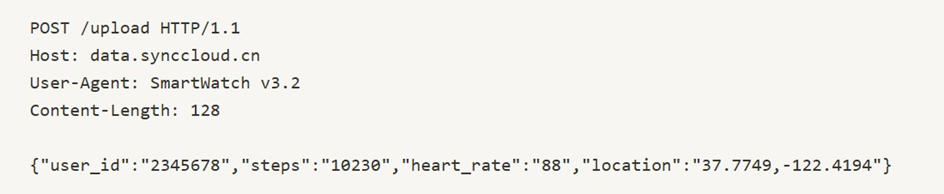
This confirms the watch is secretly sending user data to a remote server.
Phase 5:
Exploitation & Mitigation
Having identified security flaws, Akhil attempts to exploit them.
Tasks:
- Privilege Escalation – Searching for ways to gain root access.
- Firmware Patching – Modifying the firmware to disable tracking.
- Mobile Infection Risks – Determining if the app can inject malware.
Exploitation Techniques:
- Backdoor Access via UART/JTAG – Hardcoded root credentials allow system takeover.
- Insecure API Endpoints – Weak authentication permits unauthorized data extraction.
- Malware Injection via App Permissions – Excessive permissions create attack vectors.
Attempting a Root Shell:
Akhil connects to the UART interface and logs into the smartwatchʼs shell:
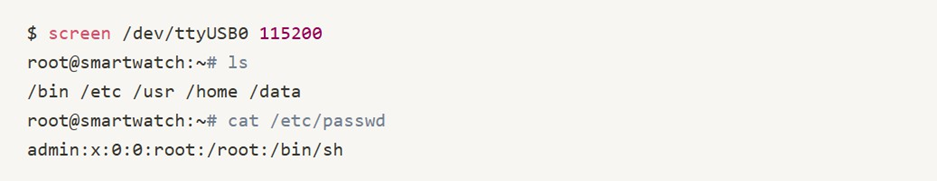
Bingo! The device has a weakly protected root account.
Lesson
Akhilʼs investigation highlights the dangers of insecure IoT devices. His research unveiled security threats which were exposing the userʼs data.
If a smartwatch can spy on you, what about other smart devices you own?