
Android Arsenal
Android Arsenal is a vast directory of Android libraries, tools, and resources, helping developers find solutions for various app development needs, including security. It offers libraries for encryption, authentication, network security, and threat detection. With categorized listings and regular updates, it ensures access to the latest security tools. Developers can explore resources for secure data storage, API protection, and malware analysis, making app development more efficient and secure.
Phase 1: Understanding Static Analysis
Akash, a budding cybersecurity enthusiast, had always been fascinated by ethical hacking. He started his mobile pentesting journey with basic tools like Apktool to decompile APK files into Smali code, allowing him to explore how apps function internally.
Wanting a deeper understanding, he experimented with Jadx, an open-source Java decompiler, to read the appʼs source code in a more human-friendly way. However, he soon realized that some apps were obfuscated, making analysis difficult. To tackle this, he tried CFR and Procyon, both advanced Java
decompilers, alongside dex2jar, which converted DEX (Dalvik Executable) files into JARs so he could analyze them using Java decompilers.
As Akash explored further, he encountered Xamarin-based apps. To analyze them, he used Xamarin-Decompress for extracting DLLs and dnSpy/ILSpy,
powerful decompilers for C# based applications. For React Native applications, he leveraged React-Native-Decompiler to reverse-engineer their JavaScript
logic.
Realizing manual static analysis was time-consuming, he began using MobSF (Mobile Security Framework), a powerful tool that provided a comprehensive security assessment, covering static and dynamic analysis.
At this stage, Akash also experimented with other APK analyzers:
- QARK: A vulnerability scanner that generated proof-of-concept exploits for detected flaws.
- SUPER: A rule-based APK analyzer that helped him automate security checks.
- ReverseAPK: Extracted and analyzed APK components automatically.
- AndroBugs: Detected security vulnerabilities efficiently.
- Androwarn: Provided malware behavior analysis.
- APKiD: Identified obfuscation methods used in APKs.
- StaCoAn: Created visual static analysis reports for better understanding.
With a strong foundation in static analysis, Akash was ready for the next phase.
Phase 2: Dynamic Analysis & Runtime Exploitation
Akash realized that static analysis alone wasnʼt enough; he needed to analyze app behavior at runtime. He set up Genymotion, Android Studio Emulator, and Nox to simulate different Android environments. For a fully pre-configured security lab, he installed AndroL4b, a virtual machine with various pentesting tools.
To analyze network traffic, he configured his emulator with:
- Burp Suite: A web proxy that intercepted and modified network requests.
- OWASP ZAP: A similar tool but with a strong focus on automation.
- Fiddler: Helped him inspect HTTP and HTTPS traffic.
To manipulate apps at runtime, he started with Frida, a powerful
instrumentation toolkit. Learning Frida scripts was overwhelming at first, so he switched to Objection, a user-friendly wrapper for Frida that provided commands like:
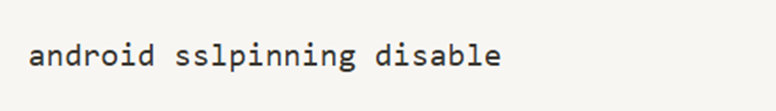
This allowed him to bypass SSL pinning easily. To further explore runtime behavior, he used:
- Inspeckage: A tool that hooked into an app to monitor API calls, permissions, and activities.
- RMS (Runtime Mobile Security): A GUI-based tool for Frida that simplified runtime analysis.
His first real breakthrough came when he used Drozer, a framework that helped him exploit Android components. By running:
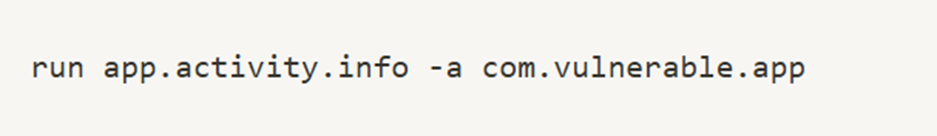
he discovered an exported activity that leaked sensitive data.
To bypass SSL pinning on apps that wouldnʼt work with Objection alone, he
used apk-mitm, a tool that modified APKs to disable SSL pinning automatically.
Phase 3: Defeating Obfuscation & Encryption
As Akash analyzed more real-world apps, he noticed that developers used ProGuard and other obfuscation techniques to hide sensitive information. To counter this, he used:
- DeGuard: A deobfuscation service that restored meaningful names to obfuscated code.
- Simplify: A tool that helped deobfuscate Java bytecode.
- APKiD: Allowed him to detect obfuscation techniques before choosing the best decompiler.
With his new skills, he could now uncover hidden secrets in complex applications.
Phase 4: Extracting Hidden Data & API Calls
Akash now wanted to analyze apps outside of official stores, so he used Evozi APK Downloader, APKPure, APKMirror, and APKCombo to obtain APKs for testing.
He also set up pidcat and adb logcat to filter app logs and capture sensitive
information such as API keys and credentials. MobSF Live API Monitor, a Frida- based tool, helped him monitor API requests in real time.
For malware detection, he integrated:
- MARA Framework: A multi-tool framework that scanned for security issues.
- Koodous: A community-driven malware analysis platform.
- VirusTotal: Integrated with MobSF for scanning APKs against multiple antivirus engines.
Phase 5: Hands-on Exploitation & Training
With all his knowledge, Akash wanted a safe environment to practice advanced attacks. He set up:
- AndroL4b: A pre-configured security VM.
- Appetize.io: An online Android emulator for testing on different devices but required subcription.
For practice, he experimented with various scripts and utilities:
- apkurlgrep: Extracted URLs from APKs to find potential API endpoints.
- Frida CodeShare: Provided a library of Frida scripts shared by the community.
- Xamarin-Decompress: Helped extract DLLs from Xamarin-based apps.
He also tested Yaazhini, a GUI-based static analysis tool, and experimented with FloatingWindowApp and QARK to understand tapjacking attacks.
He also started using APKLab, a Visual Studio Code extension that integrated with APK analysis tools.